Malicious acts aimed at disrupting digital life in general by stealing and abusing data are known as cyber dangers. Unauthorized access to, changes to, or destruction of sensitive information, money extortion, or process disruptions are examples of these acts.
Let’s take a look at the many forms of cyber risks that exist:
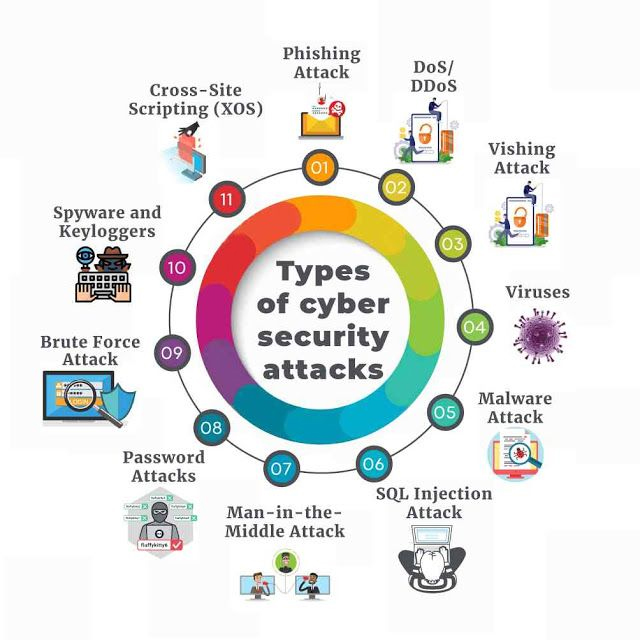
Phishing:
Phishing is a fraudulent attempt to gain personal data such as credit card information, usernames, and passwords by sending emails posing as legitimate sources. The most prevalent sort of cyberattack is phishing. It may be avoided if the public is made aware of the problem and if the newest technological solutions are used to detect fraudulent emails.
Ransomware:
Ransomware is a type of malicious software that is used to extort money. Attackers restrict access to data or systems until the victim pays a requested ransom. Paying the ransom, on the other hand, does not always ensure file recovery or system restoration, which might be a major setback.
Malware:
Malware is computer software that is meant to gain unauthorized access to computers or to harm them. Viruses, worms, ransomware, and spyware are examples of malevolent software. The program that activates the infection is installed by clicking on malicious links or attachments. It can do the following once activated:
- Data may be obtained invisibly by sending it from the hard disc (spyware)
- Users are prevented from accessing critical network components (ransomware)
- Individual components can be disrupted to render systems unusable.
- Install dangerous software that can harm your computer.
Social Engineering:
Social Engineering is a term that refers to the manipulation and a method of persuading someone to divulge sensitive information such as bank account numbers, passwords, or access to their computer in order to install dangerous software that can steal such information. Users may be more inclined to click on harmful links, sources, or malware download URLs if social engineering is used in conjunction with other cyber threats.
Persistent Advanced Threats (APTs):
APT occurs when an unauthorized user obtains access to a system or network and remains undiscovered for an extended period of time. These attacks are mostly focused on data theft and do not affect the network or computers. Traditional security measures are known to go unreported and undiscovered by APTs, yet they have been blamed for a number of significant, costly data breaches.
SQL Injection:
SQL injection is when malicious code is injected into a SQL server, allowing the attacker to intervene with queries. Entering the code into an unsecured website search field is all it takes to exploit this web security flaw. The virus leads the server to leak confidential data.
Man in the Middle (MITM):
The attacks occur when hackers manipulate a two-party transaction in order to obtain data. Such assaults might happen on any unprotected public Wi-Fi network. Attackers who use such approaches place themselves between the visitor and the network and carry out destructive actions with the aid of malware.
DoS (Distributed Denial of Service):
A Denial of Service (DoS) attack is designed to stop a system or network from responding to requests and making it unreachable to users. This sort of attack involves flooding the target with traffic in order to cause a crash. Biovus is one of the Best IT companies in India.
Visit us at: www.biovustechnologies.com